Cloud Intrusion Detection Dataset
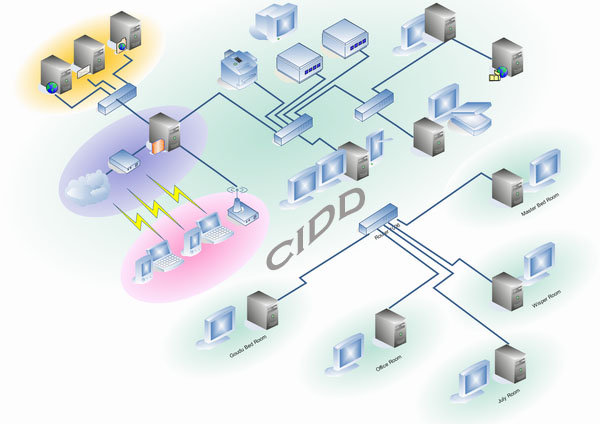
Cloud Intrusion Detection Dataset (CIDD) that solves the previous deficiencies and that includes the audits parameters to detect not only masquerade attacks but also more than one hundred instances of attacks in distinct categories. Among them, Denial Of Service (DOS), User to Root (U2R), remote to user, surveillance probing, data attacks (altering and tampering of data), and anomalous user behavior. CIDD includes both knowledge and behavior based audit data. To build the dataset, we have implemented a Log Analyzer and Correlator System (LACS), to extract user audits from a group of log files in both host and network environments. These audits have been correlated to produce the final user audit tables. LACS builds a statistical table for each user that contains among others, the number of failure logins, user login times, the IP address(es) of the user machine, list of commands and system calls issued by the user.
To overcome the difficulties and problems mentioned before, we built a Log Analyzer and Correlator System (LACS) to parse and correlate user audits from their low level format log files. We have applied LACS to logs from the DARPA Intrusion Detection Evaluation Group of MIT Lincoln Laboratory.They collected the logs and the TCP dump data from the Eyrie Air Force Base network. This network consists of two segments, representing the inside and outside of a government installation. The outside segment consists of 10 machines with Solaris, Linux, and SunOS operating systems, 1 SNMP monitor, 1 gateway, and 1 web server. The inside segment consists of 35 machines with Windows NT, Solaris, Linux, and SunOS, 1 inside gateway, and 1 inside sniffer. The network has also 2 routers and 2 hubs. These log files are mainly focus on the network audit data. However, by parsing the log files that have been collected from, respectively, one Windows NT machine, one Unix Solaris machine, and raw packet data collected from the network through TCP-dump, we have extracted the required host and network audits. We have built CIDD dataset according to both network and host audit data, we correlate between these audits according to user IP address and audit times.
We built a log analyzer and correlator system (LACS) to parse and correlate user audits from their low level format log files that we get from the
DARPA Intrusion Detection Evaluation Group of MIT Lincoln Laboratory.
For more details about LACS, Click Here